Salaam Friends! Android was originally built as an open operating system with ample opportunities. At the same time, the developers took care of security, introducing restrictions on the functionality of the programs.
The ability to fully feel like the owner of the gadget, however, remained: for this, it is enough to get the rights of the superuser.
The decision is far from everything: there is always a risk to "wry" the device, and even after root access, the question arises but is it safe to use such a smartphone? On this score, there are different points of view, and we'll try to answer this question in the article. :)
Myth: root-rights do not affect security
Modern Android-smartphones, especially gadgets of major manufacturers, are almost impossible to crack "from within".Each user Android application runs in an isolated sandbox and does not have access to other processes, and any minor important actions must be confirmed by the user. Of course, ways to get root-access "from the inside" are sometimes found, but, judging by the rare reports in the media, there is no serious impact on the security of the operating system.
That's why the vast majority of malware counts not on vulnerability, but on user's inattention, trying to trick get the right to use paid services, transferring the gadget to kiosk mode (from which it can not quit and cannot start anything) or even the device administrator status.
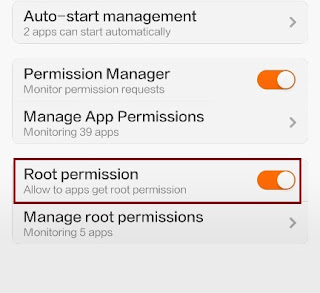
But there are devices that are sold with an unlocked bootloader or offer to get root access with a couple of clicks in the settings of the gadget.
If you decide to expand your system authority, the problems can begin already at the stage of obtaining superuser rights. All the variety of methods for obtaining root access can be divided into two categories. The first is the use of Android vulnerabilities that are not yet closed. Programs such as KingRoot or Kingo Root at runtime turn to servers that store huge exploit collections and search for those that are suitable for a particular device. Needless to say, the work of such programs often leads to sad consequences? Sometimes it happens that the exploit is working incorrectly and instead of the superuser's rights you get a "brick", which, at best, can be revived with a full re-flashing.
In addition, such applications have a closed source code, and, therefore, you have no way to know what exactly they are doing with your device.
And they can do anything, from sending data from the internal memory of the device to Chinese servers and ending with installation on the Adware gadget, which can only be got rid of by specialized tools.
This is how the above mentioned KingRoot behaves, not only placing advertisements on the home screen against your will but sending information about the device is unknown to anyone.
The second category is "semi-official" since it involves the use of official instructions from the manufacturer or specialized software to unlock the loader.
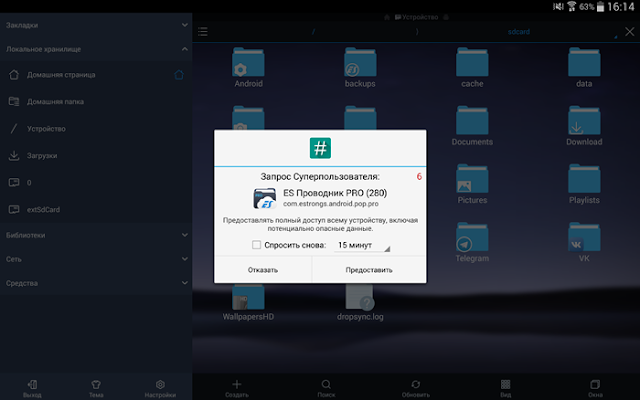
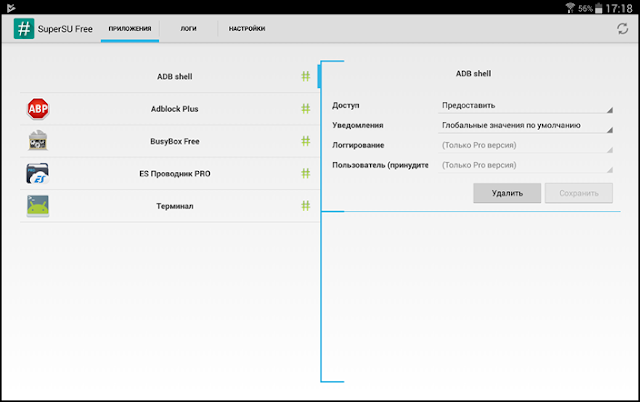
Once this is done, the user can install the root-access manager into the system, intercepting the corresponding calls from other programs.
However, this method is not devoid of shortcomings. Chainfire, the author of the most popular root access manager SuperSU, at the end of 2015, sold its development to a little-known company Coding Code Mobile Technology LLC.
This company uses the American state of Delaware as an offshore company, but its roots go to China. Source code SuperSU was closed before, but the name of the developer all this time acted as a guarantee of the absence of unwanted code in the program.
Now no one can give such a guarantee, and many are not unreasonably afraid to install SuperSU 2.80+, released after the deal, on their gadgets.
But, even if you are absolutely sure of the way of obtaining superuser rights and the root access manager, there is no guarantee that one of the programs harmless at first glance will not exploit a vulnerability that allows you to gain system privileges bypassing the manager.
Examples of malicious software working in this manner are numerous: Tordow stealthily steals passwords from the browser, Guerrilla and Ztorg bought applications on Google Play without the user's knowledge, and Triada substituted addresses in the browser, implementing almost perfect inconspicuous phishing.
 |
| According to Kaspersky Lab, one of the most advanced Trojans - Triada received root access on 247 devices |
Another cobblestone in the garden root-access - limiting the functionality of some applications or their complete inoperability after unlocking the bootloader or obtaining superuser rights. First of all, it concerns financial programs, for example, Android Pay, Samsung Pay and Sberbank Online.
Secure use of a smartphone with root access
After reading up to this point, you might have thought that we consider root-access in smartphones as an unequivocal evil.This, of course, is not true: the superuser's rights open up a huge number of opportunities for fans of third-party firmware, experiments, and just those who want to gain total control over their gadget. And if you first decided to get root-rights, we will not discourage you from this.
But you must be prepared for possible consequences, including the failure of some programs to work and increase the vulnerability of the system. It sounds unsettling, but if you observe a number of simple rules, you will hardly encounter troubles.
Install applications from reliable sources: Try to install programs only from Google Play, but remember that in the official Google store you can run into malware. If you do not have the right program on Google Play, download it from the official developer site or our forum - so the chances of meeting malware are reduced to zero.
Use proved ways to get root-rights: Do not give in to the exhortations of the developers of Chinese universal programs about the possibility to get the superuser rights in two clicks.
Use the antivirus: If you use a limited set of programs and install them from the same sources, you probably do not need an antivirus. But if you like to install dozens of different programs on your gadget or click on advertisements with "update your battery", then additional protection in the form of a proven anti-virus from a major developer will not be superfluous.
Wrapping Up
Root-access is an extremely powerful tool that requires responsibility when using.If you do not pay proper attention to each step, from unlocking the bootloader to using root privileges, you run the risk of encountering various problems, be it viruses or malicious code in the root access manager itself.
But, following our advice, you minimize all risks and can easily use applications with root-rights for their intended purpose and make the gadget completely their property.
Did you find this blog helpful? socialize with us! We hope you to share our website with your friends. It will help me get more readers and make me more motivated!
Author: MuneebShahxad [English]
Original Author: Vladimir Terekhov [Russian]
Source: 4pda.ru







0 comments: